HYDRA GTK GUI FREE DOWNLOAD
Training Resources Discussion Group Contact. Test if your Anti-Malware suite is good enough to Protect your Computer. Checking for openssl libssl, libcrypto, ssl. New Search Engine in Development Scenario: This quite considerably increases the time the attack takes but reduces the likeliness of the attack to fail. 
| Uploader: | Mut |
| Date Added: | 9 October 2012 |
| File Size: | 44.32 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 97694 |
| Price: | Free* [*Free Regsitration Required] |
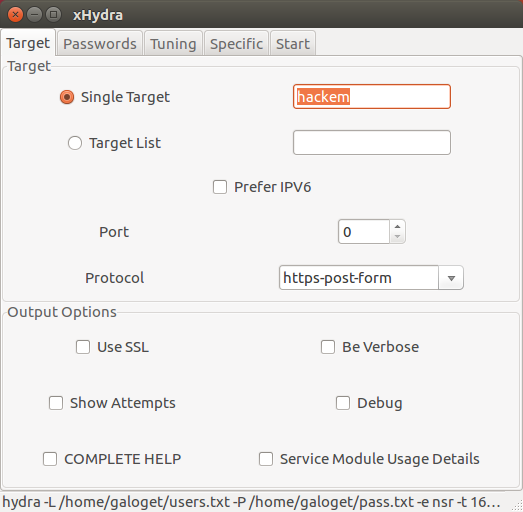
Once installed you will have a new application called xHydra, open this up and you should see a window that looks like this.
Review: Hydra / Hydra GTK - Network Logon Cracker
THC The Hackers Hyxra created Hydra for researchers and security consultants to show how easy it would be to gain unauthorized access to a system remotely. Thank you very much!!!
DNS, IP or I f you are running Kali Linux this will already be pre-installed for everyone else you can install it by typing. What is a cyber risk? Could you please compile the Hydra 8.
To set the scene here I have got Linux Mint running in my virtual lab onHow does cybersecurity work? Target's website login form.
Hey OxAli, I followed your tutorial step by step, and made it all the way until creating the launch. You can also subscribe to these comments via RSS. A malicious code had access to a small enterprise of web developers, who are gtj To get this to work you need to get some information about the login page like if its a post or a get request before you can bui your command in hydra.
In hydrs, you can use the -x to enable the brute force options. Hydra attack results with no success the password was not in the dictionary.
It always gathers a new cookie from the same URL without ttk The parameters take three ": But when I try to launch it using the code you put in launch. What is a cybersecurity architect? Is it possible to make syntax so it uses 3 known fields and 1 password.
Brute Forcing Passwords with THC-Hydra
I have been working on an adapter running Linux. And if you have any questions or problems comment or reach me at twitter 0xAli.

Path to the file that receives the form data. From Figure 4, we can extract the following information:.
CyberSecurity Forum
Name attribute of username field: You have to run launch. Command not found Makefile: So I def have to crack it… And I think the password is probably pretty complex… rainbow tables or something?

This quite considerably increases the time the attack takes but reduces the likeliness of the attack to fail. Hydra attack results with 2 valid logins.
Now Tamper Data is open click Start Tamper and it will proxy all your Firefox traffic through Tamper Data allowing us to capture the login request. As you can see below every attempt is logged in the FileZilla console you can also see all 5 login tasks running at the bottom simultaneously.
Hydra supports a wide range of network protocols including, but not limited to: In the past, VNC has been a very insecure program due to having no login name and any password could be set and it does not have to meet any complexity requirements that being said in the newer versions they have added a blacklist feature that will block you after 5 failed login attempts.
Did you search your cygwin directory properly?

Comments
Post a Comment